Yes, it's this time of the year again. There's a new wave of email making the rounds, with a message that looks as follows
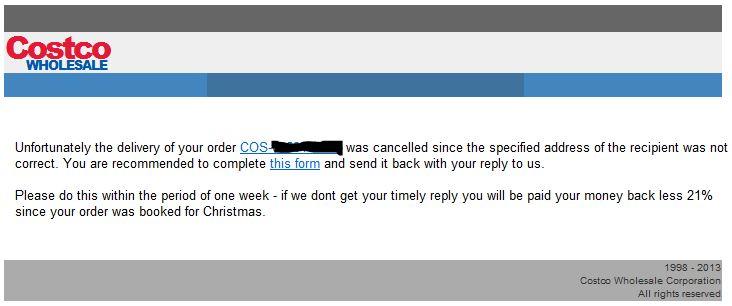
The URLs look like this
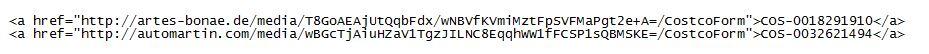
The subject seems to be one of "Delivery Canceling", "Express Delivery Failure" or "Standard Delivery Failure". Next to Costco, the same scam is currently ongoing for BestBuy and Walmart, maybe others. The links are (appear to be) random or encoded, there is no repeat occurrence of the URL and "package number" for the entire sample set that we have. It could well be that the BASE64 portion of the URL contains an encoded hash of the email address to which the phish was sent, so when you play with one of the samples, be mindful that you could be confirming the email address back to the bad guys [for that reason, the two URLs above are facsimile only, and not the real thing]
For a change, clicking on the link doesn't bring up a web form asking for your credit card number. Instead, it quite bluntly downloads a ZIP which contains an EXE. What makes this particular version more cute than others is that the EXE inside the ZIP is re-named on the fly, based on the geolocation of your download request. In my case, this spoiled the fun some, because "CostcoForm_Zürich.exe" and "CostcoForm_Hamburg.exe" didn't look all that credible: There are no Costcos in Switzerland or Germany :).
We have seen this "geolocation" approach at malware delivery used more frequently in the past weeks, for example also in a WhatsApp spam spree ten days ago. I assume someone who would click on "CostcoForm.exe" might be even more inclined to do so if the file is called "CostcoForm_DesMoines.exe" or the like, and the user is in fact residing in that same town.
As for the malware: Lowish detection as usual, Virustotal 12/44 . Malwr/Cuckoo analysis. The malware family so far seems to have a MUTEX of "CiD0oc5m" in common, and when run, it displays a Notepad that asks the user to try again later (while the EXE installs itself in the background). Further analysis is still ongoing.
Hosts currently seen pushing the malware include
bmaschool.net Address: 61.47.47.35
bright-color.de Address: 78.46.149.229
am-software.net Address: 64.37.52.95
artes-bonae.de Address: 81.169.145.149
automartin.com Address: 46.30.212.214
almexterminatinginc.com Address: 50.63.90.1
brandschutz-poenitz.de Address: 81.169.145.160
All these sites have been on the corresponding IP addresses since years, which suggests that these are legitimate web sites that have been compromised/hacked, and are now being abused to push malware.
If you have additional info on this scam, especially if you have seen the same scam for companies besides Costco, Walmart and Bestbuy, please let us know in the comments below, or share a sample via our contact form.