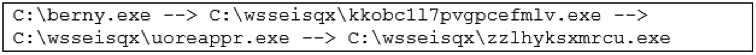[Guest Diary by Pasquale Stirparo]
Few weeks ago we witnessed a quite significant wave of email carrying with them a zip file containing an executable.
The only common thing among all the emails was that the sender name (not the sender email address) appeared to be Whatsapp or Facebook all the times, while the subject was always referring, in different languages (and sometimes terms), that You got a new audio (or video) message. Some of the subjects I saw are:
- Subject: Sie haben einen Videohinweis erhalten!
- Subject: Ein Hrbeleg ist versumt worden!
- Subject: Di recente, hai raccolto un avviso video
- Subject: Du hast eine Hrakte.
- Subject: You recently got an audible message!
- Subject: Ein akustisches Dokument wurde blo bergetragen
- ">
![]()
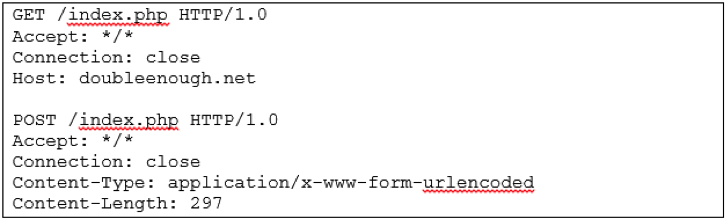
- It then tries to resolve about 40/50 domain names (on average), ">
![]()
- Do not get fooled by the eventual 404">Incidentally this very same response, as well as the server IP to contact, appears also in the report of f0xy malware, a CPU miner uncovered last year by WebSense [3]. However, the two samples are completely different.
- The malware will later upload some information about the files dropped and the email address of the victim, again base64 encoded.
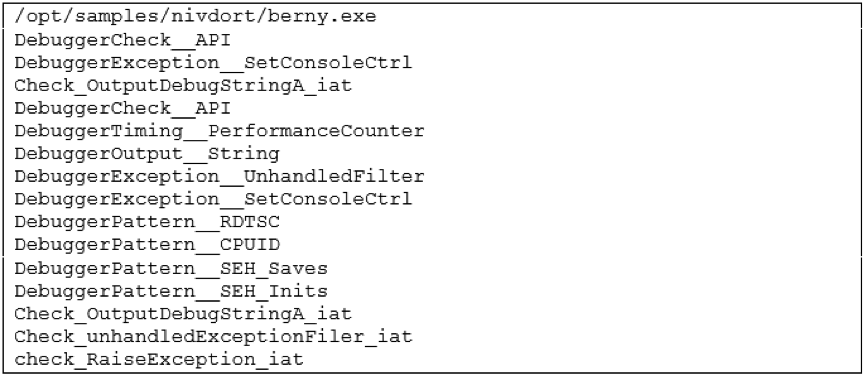
In case any of you may want to try to analyze the sample, be aware that the binary will also implement some anti-debugging techniques as detected also by running Yara against the Yara Rules from the official repository [4]
![]()
Im not sharing MD5 of the samples collected since all of them are different and would not be a much actionable information. However, you can find below a list of C2 domains which the samples tried to contact. Looking at them one may think that Nivdort does not use any DGA, instead it does use a particular DGA based on a dictionary, which makes the domains not looking random and able to bypass many DGA checks used by some filters. If you are interested to know more about it, there is a nice write up by NeutralizeThreat [5] who reverse engineered the sample and described its functionalities in details.
Happy Hunting,
Pasquale
">againstangry.net">againstarticle.net">againstdried.net">againstfifteen.net">betterbehind.net">betterbroad.net">betterbutter.net">betterunderstand.net">breadbehind.net">breadbroad.net">breadbutter.net">breadunderstand.net">captainangry.net">captainarticle.net">captainbehind.net">captaindried.net">captainfifteen.net">decideangry.net">decidearticle.net">decidedried.net">decidefifteen.net">doubtangry.net">doubtarticle.net">doubtdried.net">doubtfifteen.net">electricbehind.net">electricbroad.net">electricbutter.net">electricdried.net">electricunderstand.net">flierbehind.net">flierbroad.net">flierbutter.net">flierunderstand.net">gatherbehind.net">gatherbroad.net">gatherbutter.net">gatherunderstand.net">largeangry.net">largearticle.net">largebutter.net">largedried.net">largefifteen.net">nightangry.net">nightarticle.net">nightdried.net">nightfifteen.net">quietbehind.net">quietbroad.net">quietbutter.net">quietunderstand.net">recordbehind.net">recordbroad.net">recordbutter.net">recorddried.net">recordunderstand.net">seasonbehind.net">seasonbroad.net">seasonbutter.net">seasondried.net">seasonunderstand.net">streetbehind.net">streetbroad.net">streetbutter.net">streetunderstand.net">tradebehind.net">tradebroad.net">tradebutter.netReference:[1] https://www.microsoft.com/security/portal/threat/encyclopedia/Entry.aspx?Name=TrojanSpy:Win32/Nivdort.AL#tab-link-3 [2] https://www.microsoft.com/security/portal/threat/encyclopedia/entry.aspx?Name=TrojanSpy:Win32/Nivdort.A[3] http://community.websense.com/blogs/securitylabs/archive/2015/01/30/new-f0xy-malware-employs-cunning-stealth-amp-trickery.aspx[4] https://github.com/Yara-Rules/rules/[5] http://www.neutralizethreat.com/2015/12/nivdort-code-obfuscation-and-dga.html
--
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
Alex Stanford - GIAC GWEB GSEC,
Research Operations Manager,
SANS Internet Storm Center
/in/alexstanford
- Do not get fooled by the eventual 404">Incidentally this very same response, as well as the server IP to contact, appears also in the report of f0xy malware, a CPU miner uncovered last year by WebSense [3]. However, the two samples are completely different.
- It then tries to resolve about 40/50 domain names (on average), ">